- Posted by :Admin
- Date :10 Jul, 2024
- Category : Tools , Features
Bridging MITRE ATT&CK & ATTACKIFY for Advanced Threat Actor Emulation
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is crucial. Today, we’re excited to introduce a new tool that bridges the gap between threat intelligence and practical security testing in ATTACKIFY : the ATTACKIFY Threat Actor Campaign CLI tool. This CLI tool combines the power of MITRE ATT&CK’s comprehensive threat intelligence with ATTACKIFY ‘s robust simulation capabilities, offering a quick and easy way to APT emulation and security testing your security controls to the latest APT reports from Mitre ATT&CK.
Understanding MITRE ATT&CK
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. It provides a comprehensive matrix of known threat actor behaviors, organized into tactics, techniques and procedures (TTPs). This framework has become an essential resource for cybersecurity professionals, offering insights into how threat actors operate and how to defend against their methods.
Leveraging ATT&CK for Threat Actor Emulation
One of the most valuable aspects of the ATT&CK framework is its documentation of Threat Actor Groups. These profiles detail the techniques and procedures used by specific adversary groups, providing a blueprint of their typical attack patterns. By understanding these patterns, security teams can better prepare their defenses against real-world threats.
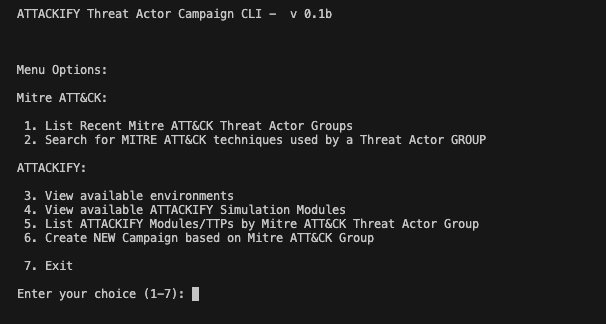
Introducing the ATTACKIFY CLI Tool
The ATTACKIFY Threat Actor Campaign CLI tool is designed to help bridge the gap between threat intelligence and practical security testing in ATTACKIFY . It leverages the MITRE ATT&CK framework to identify relevant techniques used by specific threat actors and maps these to ATTACKIFY ‘s simulation modules. This allows security teams to rapidly create and execute tailored threat emulations based on real-world adversary behaviors.
Key Features of the ATTACKIFY Tool:
Threat Actor TTP Lookup: Search for & list all techniques associated with a specific threat actor group.
Techniques Module Mapping: Automatically map ATT&CK techniques to relevant ATTACKIFY modules.
Campaign Generation: Create campaigns in ATTACKIFY based on threat actor profiles from ATT&CK.
Recent Threat Group Listing: Stay updated with the latest threat actor groups in the ATT&CK database.
ATTACKIFY Campaigns: Stringing Together Realistic Threat Scenarios
A key feature of ATTACKIFY is its campaign functionality. Campaigns allow users to string together multiple ATTACKIFY modules, creating complex, multi-stage attack simulations. This capability is crucial for testing security controls against sophisticated, real-world attack scenarios in full context.
With the introduction of the ATTACKIFY CLI ool, creating these campaigns becomes even more powerful. Users can now automatically generate and run campaigns based on the TTPs of known threat actor groups. This allows for the rapid creation of highly realistic threat actor emulations, closely mimicking the behavior of specific adversaries.
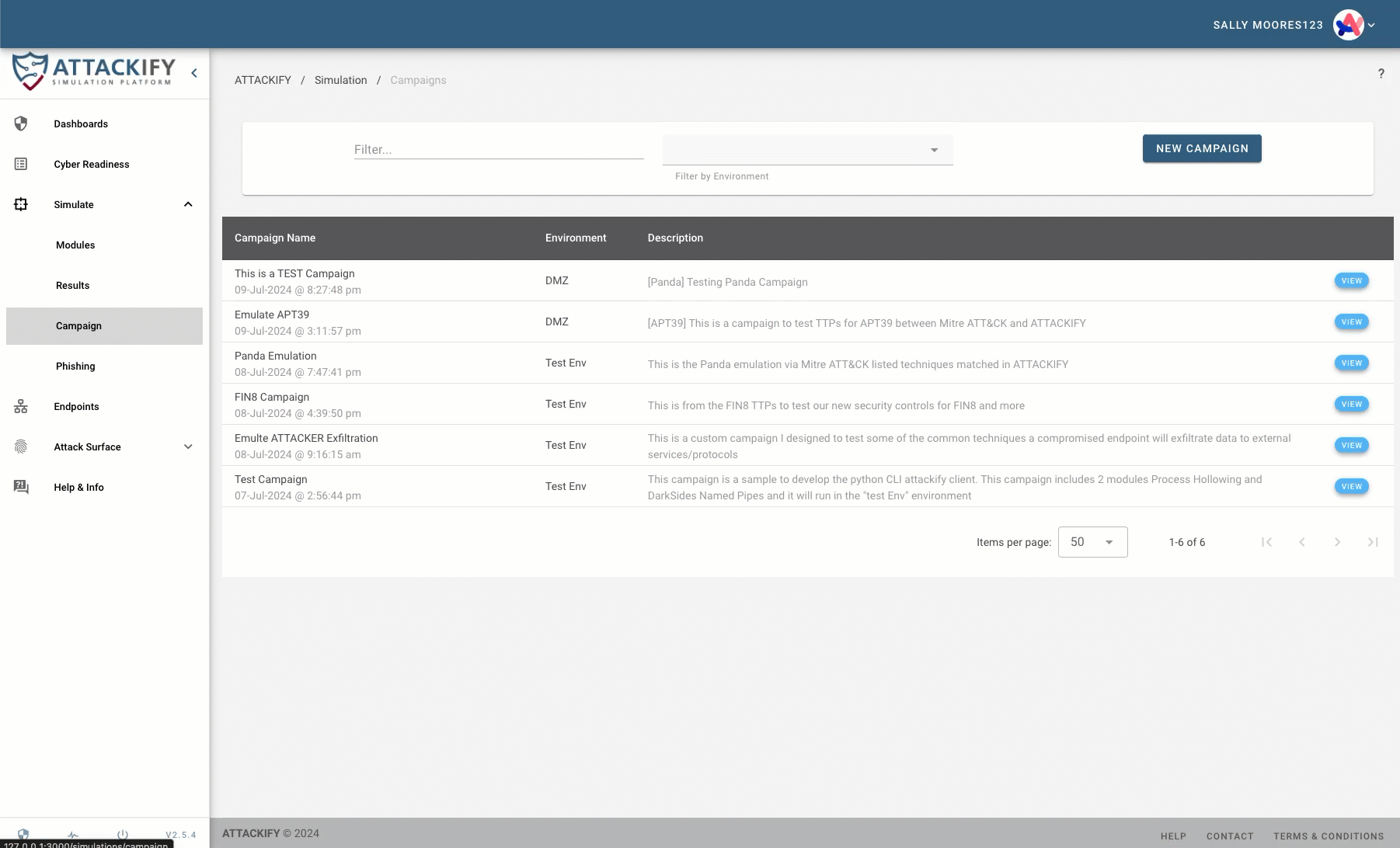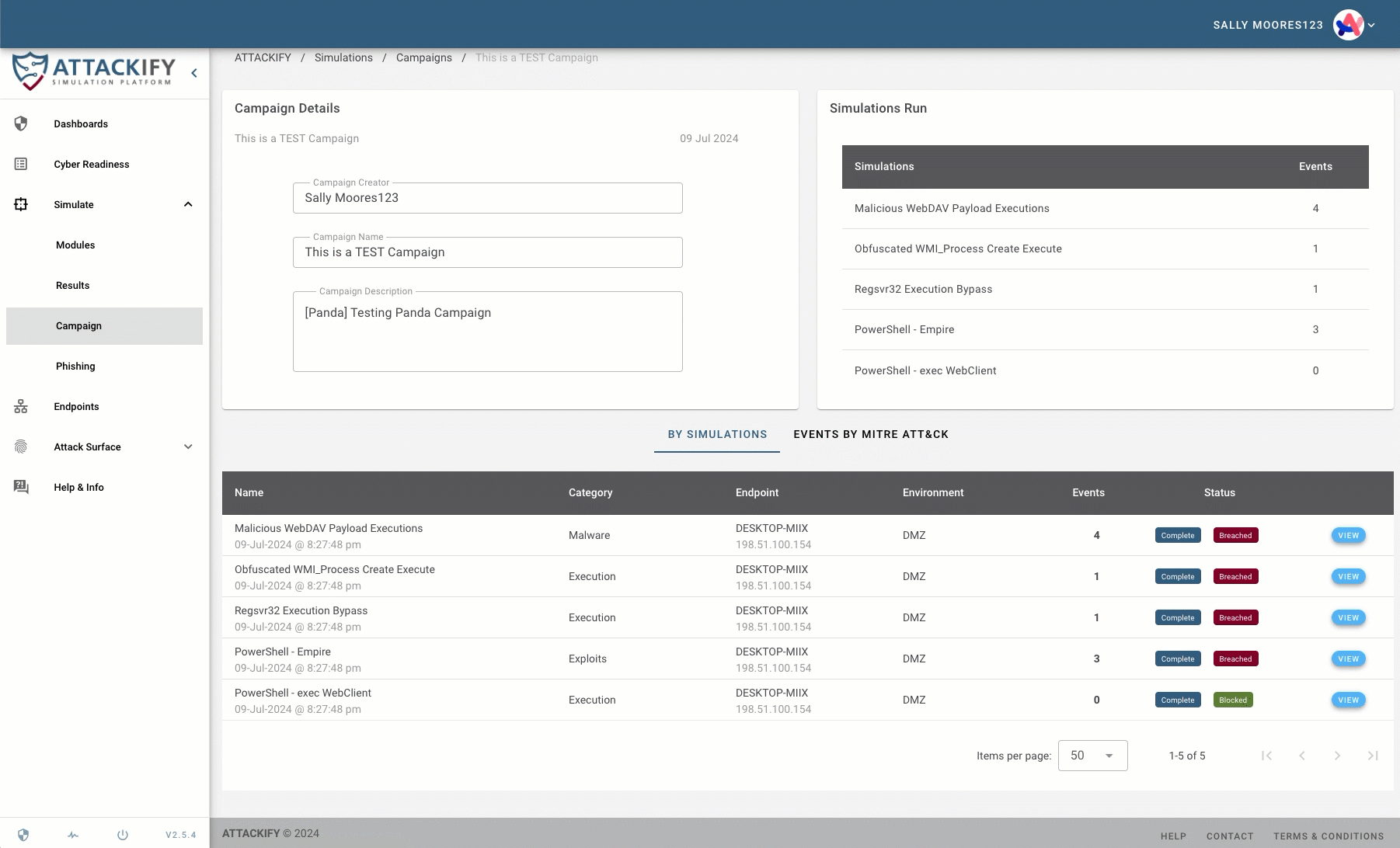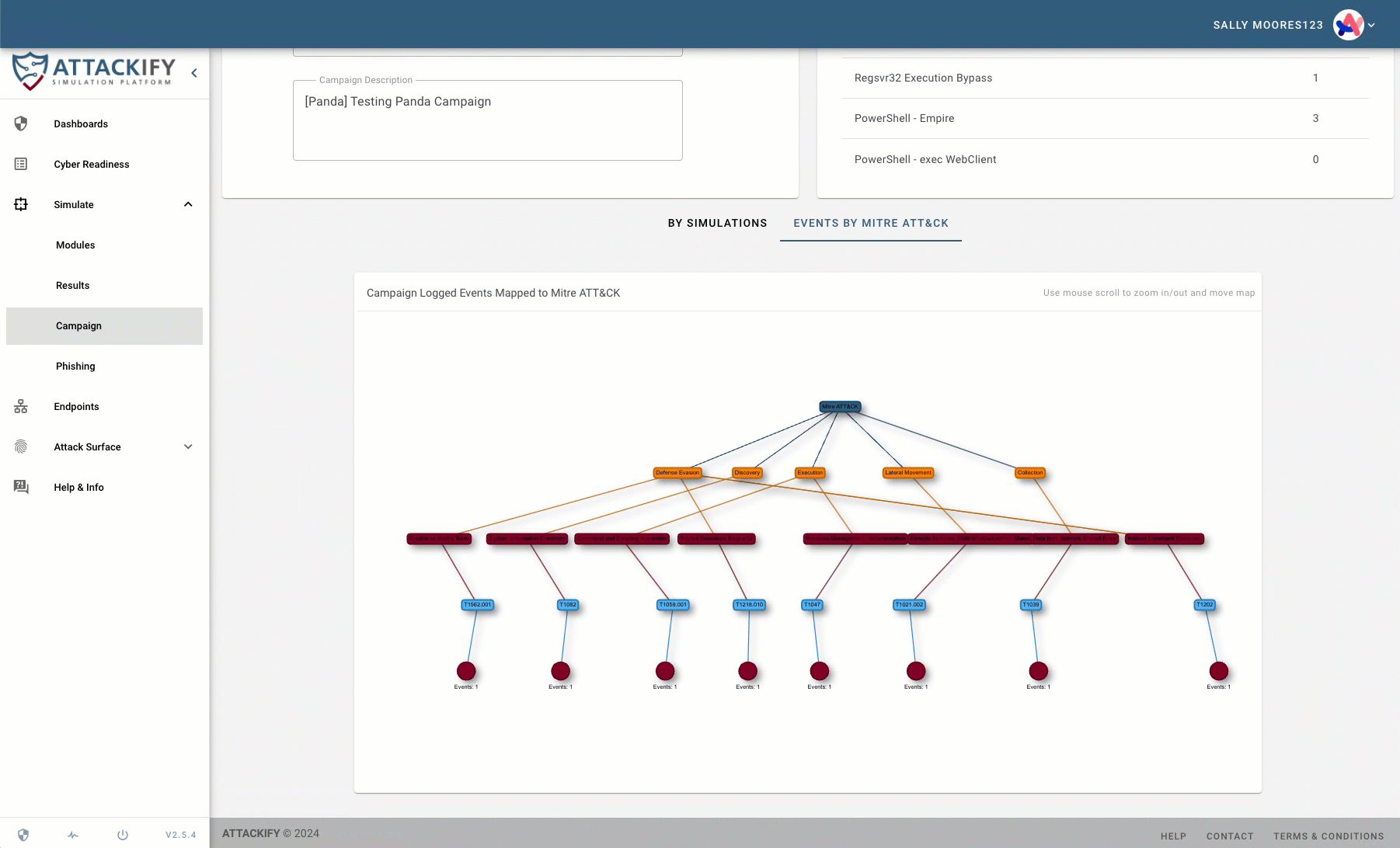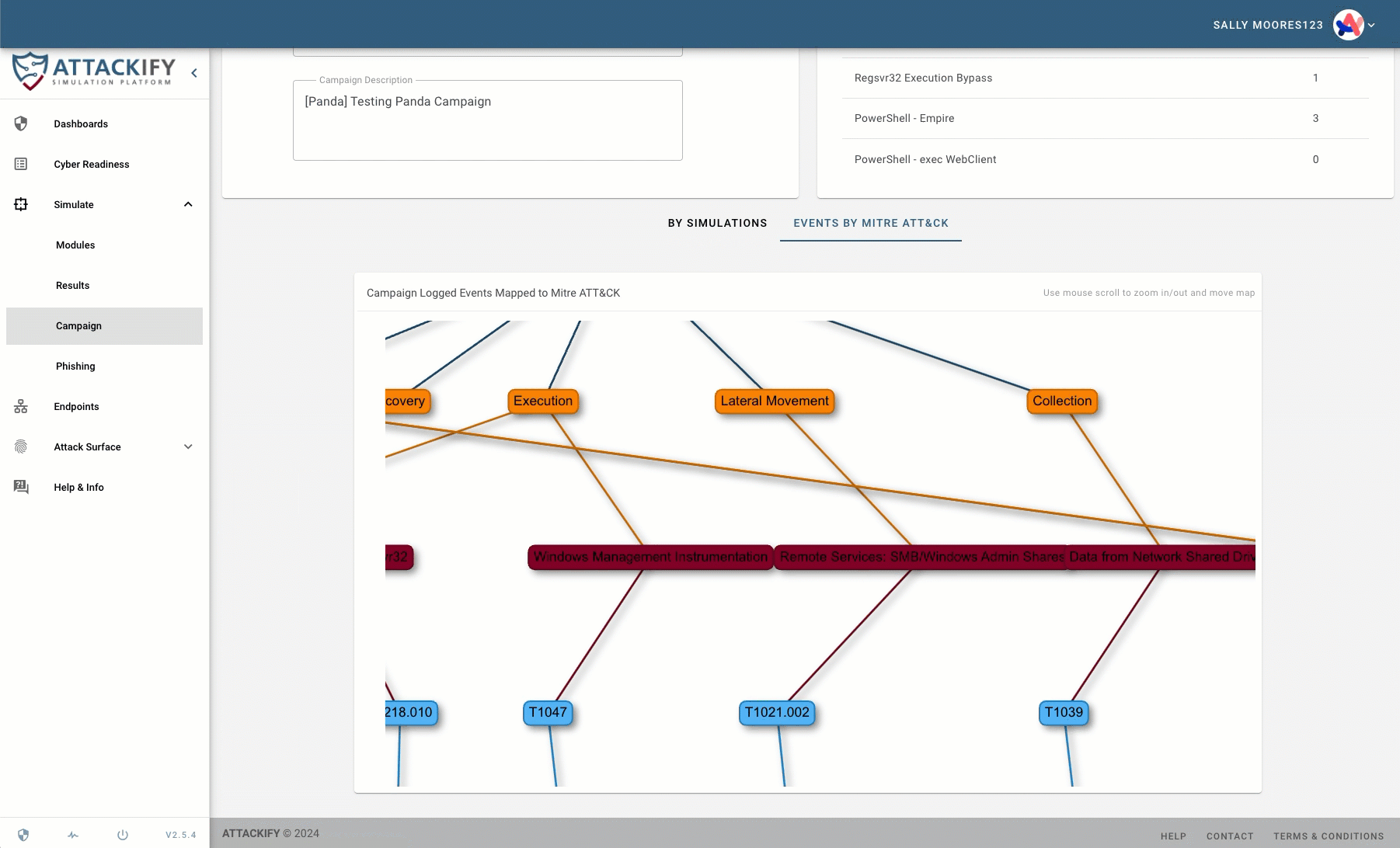
Emulating Threat Actor Groups
The primary goal of the CLI tool is to facilitate the easy emulation of threat actor groups. By automating the process of mapping Mitre ATT&CK techniques to ATTACKIFY modules and running campaigns automaticallt, security teams can quickly set up and execute emulations that closely resemble the TTPs of specific adversaries. This capability allows for more targeted and relevant security testing, helping organizations prepare for the threats most likely to target their industry or sector.
Beta Release and Future Development
We’re excited to announce that this first version of the ATTACKIFY Tool is now available as a beta release. As with any beta software, we encourage users to provide feedback and report any issues they encounter. Your input will be invaluable in refining and improving the tool.
In future versions, we plan to expand the tool’s capabilities, potentially including features such as:
- Custom technique-to-module mapping- Integration with additional threat intelligence feeds
- Advanced campaign scheduling & automation
- Detailed reporting & analysis of campaign results
- Expand the CLI tool to cover more ATTACKIFY features & automation
Conclusion
The CLI Tool although small and in its early phase represents making a faster step forward in making advanced threat emulation accessible and actionable but most of all, EASY. By bridging the gap between MITRE ATT&CK’s threat intelligence and ATTACKIFY ‘s simulation capabilities, we’re empowering security teams to test and improve their defenses against the most relevant and sophisticated threats.
We invite you to try out the ATTACKIFY Tool and experience firsthand how it can enhance your security testing and threat emulation capabilities. Together, we can build more resilient defenses against the ever-evolving threat landscape.
To automagically run Threat Actor Groups from Mitre ATT&CK within ATTACKIFY , Campaign does require a PROFESSIONAL account. You can still run the tool with a FREE tier to extract mappings between ATT&CK TTPs and ATTACKIFY modules
Visit the GITHUB repository here: Threat Actor Campaign CLI