
- 25 Apr, 2024
- Admin
ATTACKIFY Partners with Tidal Cyber for Enhanced Threat Defense
Partnering with Tidal Cyber for Enhanced Threat Defense We are excited to announce a partnership …
Read MoreATTACKIFY is a comprehensive cloud-based platform engineered to facilitate and streamline a wide array of cyber security operations & designed to empower organizations of all sizes to enhance their digital defenses against an evolving landscape of cyber threats, by providing:
Breach & Attack Simulations
Endpoint Security Audits
Phishing Simulations
Attack Surface Discovery & Vulnerability Scanning
Cyber Security Readiness Assessments
Conceived as an all-encompassing solution, ATTACKIFY offers organizations an accessible and cost-effective solution for addressing multiple cyber security needs within one unified framework. ATTACKIFY democratizes access to advanced cybersecurity tools, making it easier for organizations to test, identify, and fortify their defenses against cyber threats.
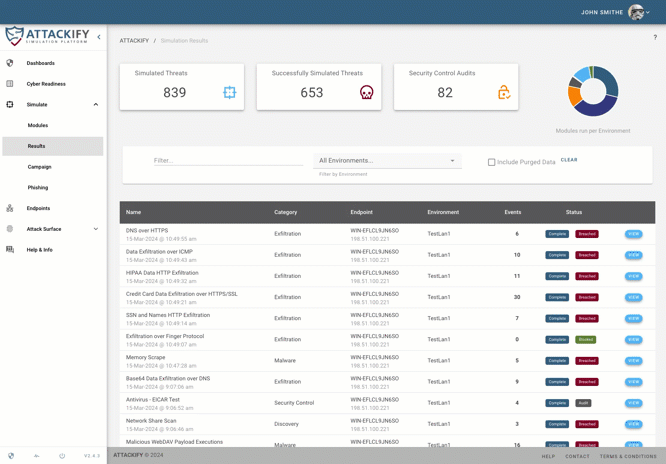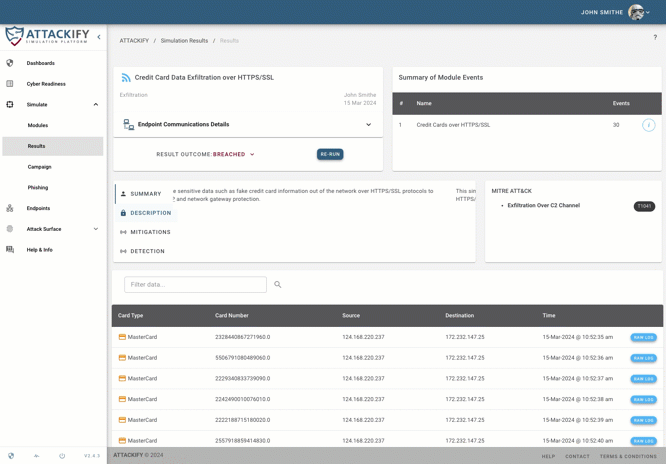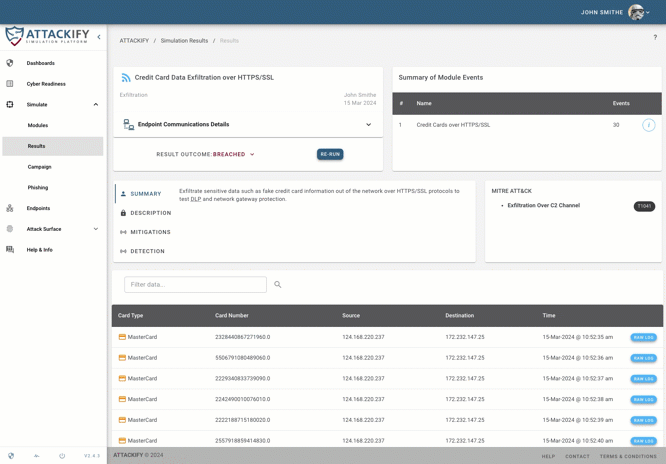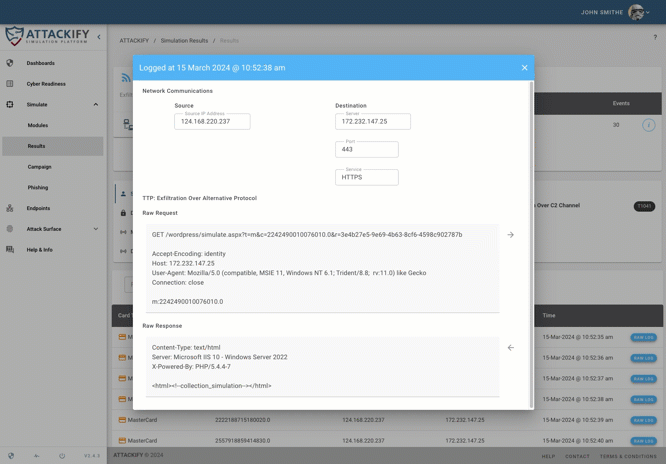

The ATTACK module library allows you to run real-world cyber threats and is constantly being updated and expanded with the latest TTPs, enabling organizations to simulate attacks from existing, new & emerging cyber threats, SAFELY within your own environments.
ATTACKIFY doesn’t just simulate threats; it also features modules to audit endpoint security controls, policies, and validate remedial actions. Use ATTACKIFY to validate against industry best practices & compliance frameworks and scan for vulnerable software inventory CVEs.
Conduct targeted PHISHING drills and emulate RANSOMEWARE & SOCIAL ENGINEERING modules to gauge user security awareness at your organization and measure the efficacy of security safeguards and controls in your environment.
Utilizing some of the best open-source tools, ATTACKIFY has integrated an ATTACK SURFACE module into the platform. Use ATTACKIFY to discover your organizations ASSETS exposed to the Internet and scan them for VULNERABILITIES.
ATTACKIFY isn’t all about run SCANS and SIMULATING attacks, you can perform continous self assessments to evaluate your current CYBER SECURITY READINESS maturity & posture. We provide additional guidance based on your results to improve core areas and raise your overall posture.
Utilizing the MITRE ATT&CK® framework, ATTACKIFY delivers comprehensive detection and mitigation strategies, complemented by pertinent SIGMA rules.
Breach & Attack Simulation doesn’t get any easier than ATTACKIFY . If you have ever tried to setup and use Atomic Red (which is great by the way) or try find your way through a really expensive and complex BAS solution and just want to get to the good stuff, then ATTACKIFY is for you.
ATTACKIFY is designed to be easy to use and easy to understand. We have taken the complexity out of the platform so you can focus on running ATTACK simulations. Login, download and run an endpoint agent, select a module and run it. It’s that simple.
ATTACKIFY is designed to be used by anyone, from the most junior analyst to the most senior security professional, even your CISO could run ATTACKIFY.

Partnering with Tidal Cyber for Enhanced Threat Defense We are excited to announce a partnership …
Read More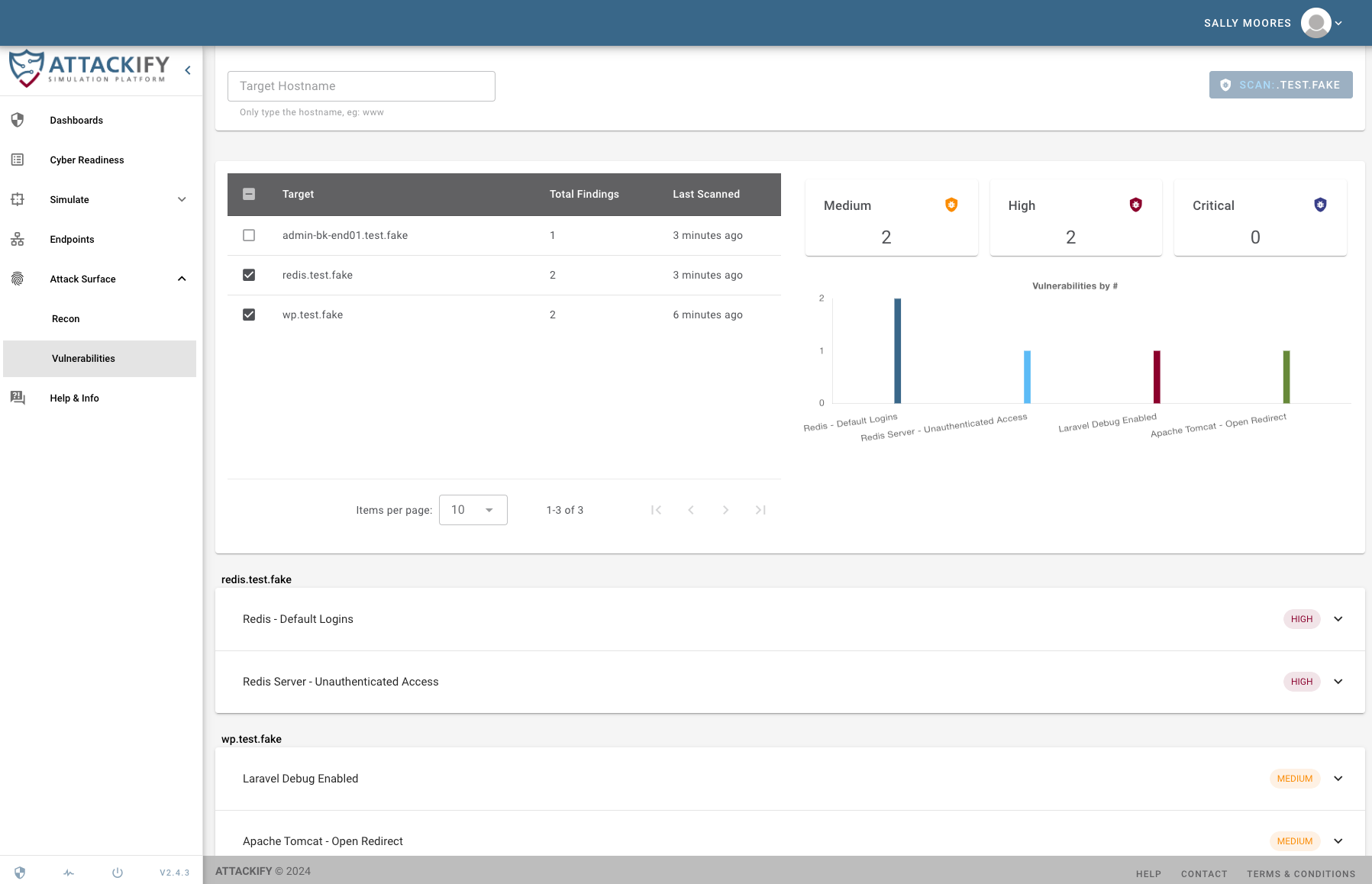
Introducing Attack Surface Management In the ever-evolving landscape of cyber threats, staying ahead …
Read More
Introducing the Scheduler At ATTACKIFY, our mission has always been to offer an agile, automated, …
Read More